
Securing the microelectronics supply chain
The Secure, Trusted, and Assured Microelectronics Center at Arizona State University advances the security of microelectronics and the domestic workforce pipeline
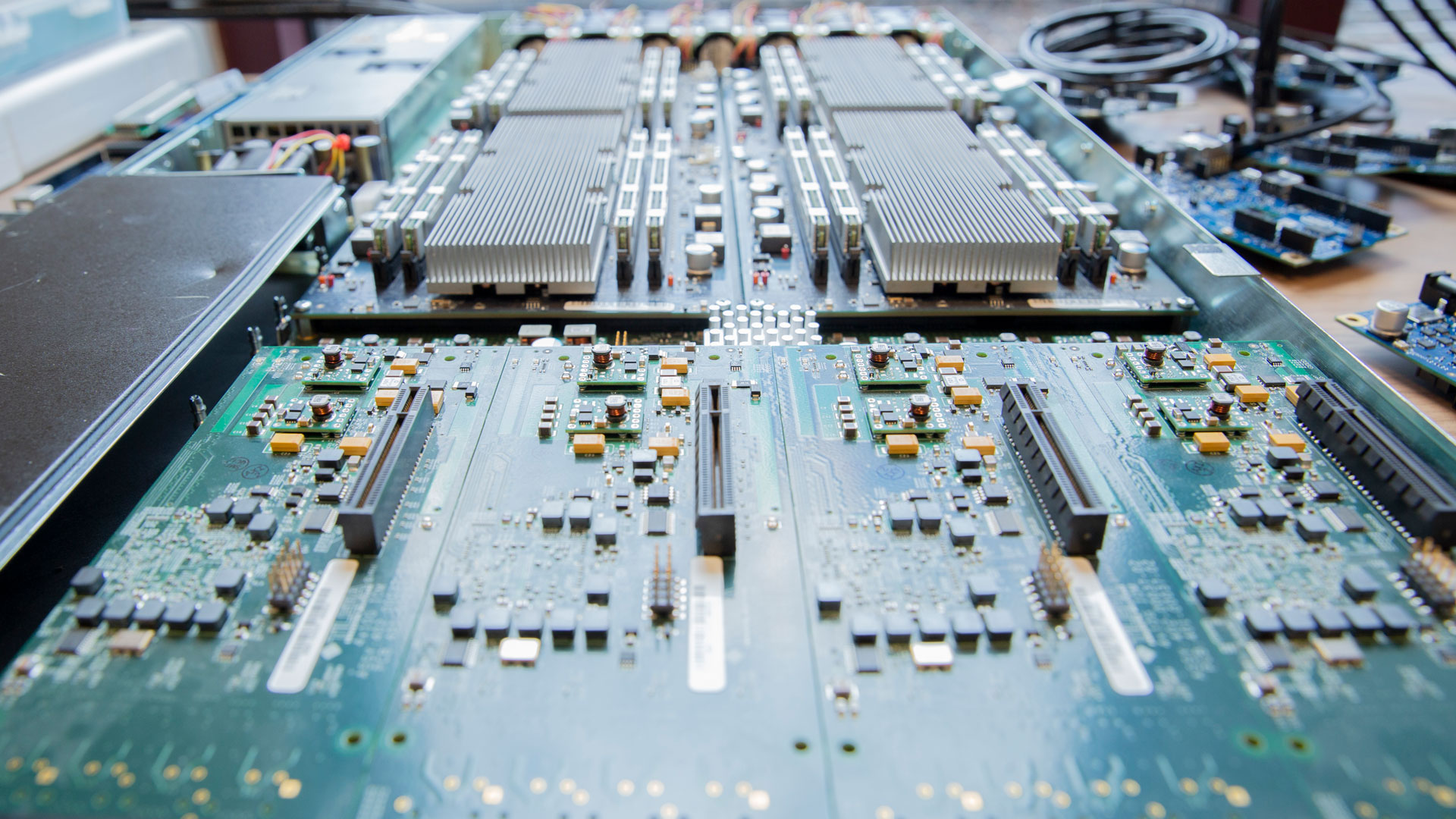
Microelectronics enable all of the electronic systems we use today, from pacemakers, voting machines and cars to airplanes, missiles and supercomputers.
Also known as semiconductors, microelectronics have a uniquely complicated production supply chain. A typical semiconductor’s production occurs on multiple continents and takes three or more trips around the world, spanning 25,000 miles, according to a report by the Semiconductor Industry Association.
Over the course of this journey, many security challenges arise. Counterfeiting is a prevalent example. Between 2007 and 2010, U.S. Customs officials seized more than 5 million counterfeit microchips destined for commercial aviation and military applications. This problem has only increased due to supply chain issues and the resulting chip shortages during the COVID-19 pandemic.
Additional security issues include stolen intellectual property and design reverse-engineering. Along the supply chain, people can manipulate quality control information to pass lower-quality microchips as military-grade for a higher resale price. During production, malicious circuits or components could also be added and activated later to steal critical user information or disrupt the proper function of the device, such as a car failing to stop at a red light or a missile striking an unintended location.
“Hardware-based attacks are a particularly insidious form of cyberattacks,” says Michel A. Kinsy, an associate professor of computer systems engineering in the Ira A. Fulton Schools of Engineering at Arizona State University. “When an attacker is leveraging hardware to mount the attack, it is truly an electronic kneecapping. They are attacking you from within the computing core. There is very little your software or software security apparatus or tools can do.”
When electronic devices have a backdoor that allows attacks to bypass all defense mechanisms and roam freely within the system, serious danger can result. This is an especially high risk in electronics applications in which safety and reliability are paramount, including defense and military equipment, aviation and automotive transport systems, medical electronics, telecommunication and electric grid infrastructure.
“Our national security, economy and even our civil liberties are at risk without adequate security and trust in microelectronics,” Kinsy says.
Filling a gap in the microelectronics industry

Michel Kinsy, an associate professor of computer systems engineering in the Fulton Schools, is director of the STAM Center. Photographer: Erika Gronek/ASU
The key barrier to developing more secure electronics, Kinsy says, is “chronic under-investment in the domestic microelectronics design, development and manufacturing base” and a lack of education and training for the microelectronics workforce.
“Students and professionals, even those in the field of cybersecurity, have little to no exposure to microelectronics design and testing, and techniques to improve their security and trust,” Kinsy says. “Yet, microelectronics anchor the security and trust of the system.”
To help advance research into microelectronic security and workforce development, Kinsy established the Secure, Trusted, and Assured Microelectronics, or STAM, Center at the Fulton Schools.
“We aim to catalyze a uniquely integrated effort between academia, government and industry stakeholders to innovate around related topics and broaden participation in the field with real-world relevance and significance,” Kinsy says.
Phoenix and ASU are highly attractive for such a center. The metropolitan area around Phoenix has established itself as a national hub for semiconductor manufacturing, with facilities for leading manufacturers Intel Corporation, onsemi, NXP Semiconductors, Microchip Technology and others. Additionally, ASU’s priorities of access and inclusion will help with the center’s goals of educating and training all segments of the population.
“ASU having one of the largest, most comprehensive engineering colleges in the country and in a region of the country that is emerging as a leader in the semiconductor industry with a high concentration of microelectronics research and fabrication activities provides the STAM Center a unique opportunity to have lasting societal impact,” Kinsy says.
Advancing microelectronics security through innovative research

Michel Kinsy works with Graduate Research Associate Alan Ehret (right), the interim lead of the STAM Center’s Computer Architecture and Embedded Systems Laboratory. The STAM Center is organized into two technology laboratories and four application laboratories that complement each other and collaborate on projects. Photographer: Erika Gronek/ASU
The good news about microelectronics challenges, Kinsy says, is that there are new technologies and techniques being developed to improve security and trust.
Agencies like the U.S. Department of Defense are adopting “zero trust” policies, which assume no microelectronics are safe and all must be validated. Validation can take the form of using advanced imaging technologies and forensics methods to detect counterfeits and malicious circuits. Components can be marked or tagged to authenticate and track supply chain movements. Additional technologies can be applied to prevent exploitation and counter security threats.
The STAM Center’s role in advancing microelectronics security is to investigate emerging microelectronics technologies, new computation paradigms and new secure hardware root-of-trust techniques through research and development.
The center takes a highly integrated approach to its organization with two technology laboratories and four application laboratories.
The two technology laboratories focus on developing new components for microelectronics. The Semiconductor Security Laboratory, or SemiSec, focuses on low-level, secure integrated circuit, or IC, design, while the Laboratory for Unconventional Computing Substrates, or LUCS, investigates emerging substrates and post-CMOS technologies. CMOS, or complementary metal-oxide-semiconductor, is the main underlying design of modern ICs.
The application laboratories take the new components developed in the technology laboratories to develop new computing systems. The Adaptive & Secure Computing Systems Laboratory, or ASCS, develops situation-aware, adaptive secure computing and self-healing computing systems. The Artificial Intelligence Technology and Systems Laboratory examines secure and privacy-preserving AI/ML systems. The Computer Architecture & Embedded Systems Laboratory designs secure, high-performance computing architectures. The Secure & Resilient Cyber-Physical Systems Laboratory focuses on the deployment of microelectronics in critical infrastructures.
Each laboratory’s focus area is meant to complement the others to design and prototype application-driven, complete, secure and trustworthy systems that demonstrate real-world impact. Projects span multiple laboratories and incorporate each other’s resources and their researchers’ expertise.
“This strategic approach provides the center with a strong differentiating factor and enables a faster path to commercialization,” Kinsy says.
STAM Center researchers are exploring IC security through vertically stacked ICs in a technique called 3D integration. They are also exploring counterfeit-resistant and anti-cloning design methodologies, along with other design obscuration and masking techniques that use self-adaptation to automatically react to threats.
Through artificial intelligence and machine learning applications, researchers are developing methods for defending against hardware and intellectual property theft.
The research teams are also developing trusted circuit analysis tools with hardware-in-the-loop simulation capabilities and techniques to keep data and identities private.
Other projects focus on developing a cost-effective approach to comprehensively test how electronic components will perform in the end product.
The STAM Center’s work continues to evolve to address emerging real-world challenges in microelectronics security. With counterfeit threats increasing during the pandemic, the researchers’ work has accelerated in this area.
“We were able to collect more chips and identify new counterfeit techniques,” Kinsy says.
Training the next generation of microelectronics professionals
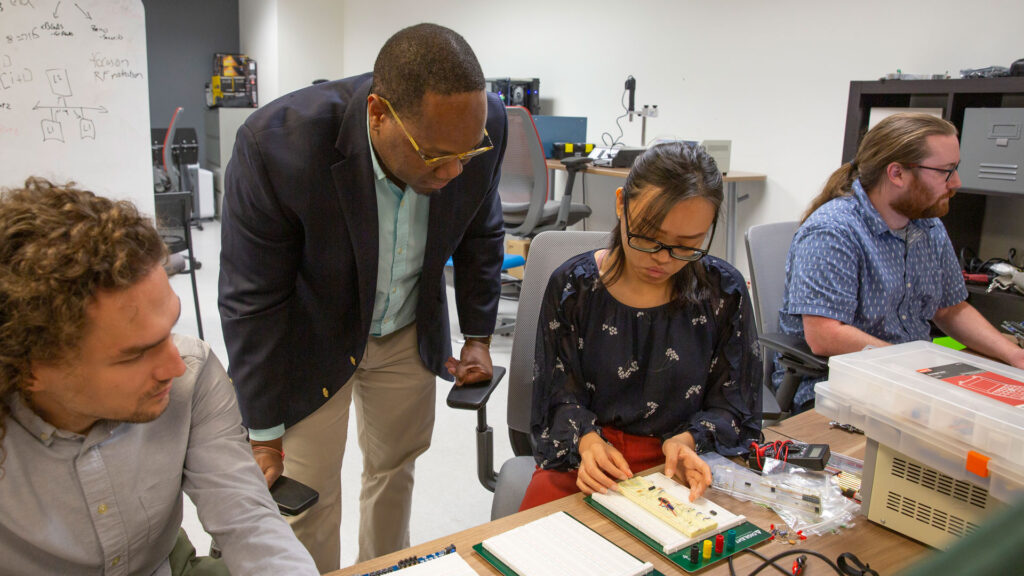
Michel Kinsy works with graduate students in the STAM Center. From left to right: Mihailo Isakov, computer engineering graduate student and interim lead of the Artificial Intelligence Technology and Systems Laboratory; Minh Huynh, a computer science graduate student and graduate research associate; and Alan Ehret, a computer engineering graduate student and CAES Laboratory interim lead. An important goal of the STAM Center is to help build up the local workforce to strengthen the semiconductor industry in Phoenix. Photographer: Erika Gronek/ASU.
Kinsy earned bachelor’s degrees in computer science and computer systems engineering from ASU nearly 15 years ago and returned to the university as a faculty member in 2021.
“One consistent thought I have about ASU’s computer systems engineering program over the years is how well it prepared me,” Kinsy says. “It is very impressive to see how ASU has continued to transform and grow since my undergrad years. It is a great joy to be able to add to that. As a faculty member now, I would like to shore up the graduate computer systems engineering program with a stronger emphasis in hardware and microelectronics security.”
Beyond curriculum in the Fulton Schools, Kinsy aims for the STAM Center to help build up the local workforce to keep and attract semiconductor companies in the Phoenix area.
“Without a robust and highly skilled workforce, the semiconductor industry does not take root,” he says. “Just 20 years ago, the U.S. was manufacturing 40% of the world’s microchips. Today, we are down to about 11%. This erosion mirrors the educational investment trend.”
Kinsy is helping to develop an exposure and outreach pipeline program of Saturday electronics design workshops, seminars, webinars, short- and long-term professional development training courses and a certification process. Collaboration with local semiconductor companies includes regular industry open-house events, research and development partnerships and student internship and job placement programs.
Recently, the STAM Center launched the Arizona Cyber Range, or AzCR, a training platform for security issues related to hardware/electronic devices. Trainees will have access to microcontrollers, industrial control systems, Internet of Things devices and more, and can explore the systems through virtual environments to learn valuable skills.
“Our short-term objective is to serve the local Phoenix microelectronics industry and use our local success to establish a national standing for creating a sustainable research training program in secure and trusted microelectronics,” Kinsy says.
“Phoenix is the perfect environment to ensure that the STAM Center’s research, education and outreach efforts reflect the composition of the larger U.S. population,” he says. “We want to serve as a national model for recruiting, engaging and training nontraditional students and U.S. military veterans — especially those from underrepresented groups and underserved communities.”

STAM Center researchers are making real-world impact through innovative microelectronics and computing research. Photographer: Erika Gronek/ASU



































