
Award-winning cybersecurity startup springs from ASU research

Graphic courtesy of Pixabay
In 2013 Paulo and Jana Shakarian collaborated on a book that explored cyberwarfare from “a human-centric viewpoint,” as Paulo Shakarian describes it.
“We noticed that everyone who was working on cybersecurity was focused on the technical aspects of it. Things like building firewalls and doing virus scanning,” he says. “But no one was taking a deep look at the people who are doing the bad stuff, the cyber attackers.”
The theme of the book became the genesis of the research they’ve done to understand the “hacker ecosystem” and devise ways to not merely respond to cyberattacks but to predict and thwart them in advance.
That research has given birth to CYR3CON, which the Shakarians define as “a next-generation cyber threat intelligence company” that employs machine learning, data mining and artificial intelligence technology — along with knowledge of the workings of the dark web — to identify emerging threats.
More than that, CYR3CON’s system guides users in making informed decisions about what cyber defense actions should be launched to most effectively neutralize specific kinds of hacking attempts.
Combining their expertise to explore cyber world
CYR3CON was started and is led by the Shakarians, who are husband and wife. Paulo Shakarian is the company’s chief executive officer. Jana Shakarian is the president.
Paulo Shakarian’s expertise is in cybersecurity, artificial intelligence and social network analysis. He is director of the Cyber-Socio Intelligent Systems Laboratory at Arizona State University, where he is a Fulton Entrepreneurial Professor in the Ira A. Fulton Schools of Engineering.
He has been named a Knowledge Discovery and Data Mining Rising Star by Microsoft Research, held a fellowship with the U.S. Defense Advanced Research Projects Agency and won an Air Force Young Investigator award for his work in cybersecurity. He was also awarded a Bronze Star for his Army service, which included two tours in Iraq.
Jana Shakarian is a sociologist and anthropologist specializing in the behavior of hacking groups, and co-author of several books on topics relating to malicious hacking and terrorism. She previously worked as a staff social scientist for the University of Maryland Institute for Advanced Computer Studies. In her current role, she works with ASU’s Center for Cybersecurity and Digital Forensics.
Paulo Shakarian is on the faculty of the School of Computing, Informatics, and Decision Systems Engineering in the Fulton Schools. Jana Shakarian is an assistant research technologist in the same school.
The expertise employed in the Shakarians’ venture mirrors an array of major research thrusts at ASU, particularly in the Fulton Schools. The range spans from such pursuits as digital forensics, web and data mining, and computer systems security modeling and architecture, to automated vulnerability analysis, cybercrime analysis and intelligent machines and systems — as well as the use of social sciences research in the development of engineering and technology solutions.
Paulo Shakarian says the CYR3CON cybersecurity venture reflects Arizona State University’s emphasis on use-inspired research that seeks to provide solutions for real-world problems — as well as ASU’s support for startups that can move new technologies into the marketplace. Video by Jamie Ell/ASU NOW
Advanced technologies for identifying vulnerabilities
Their CYR3CON venture won a TechConnect Defense Innovation Award at the Defense Innovation Technology Acceleration Challenges Summit — a meeting of leaders in defense and security industries and officials in government agencies and the U.S. military.
CYR3CON was also a finalist in the recent tech startup and business model competitions held by the Arizona Technology Council and PricewaterhouseCoopers.
The TechConnect award was specifically for the company’s product called Vulnerability Update. It’s technology that provides a constant monitoring of software vulnerabilities in cybersecurity systems that are being identified through communications between potential hackers on the dark web. Vulnerability Update identifies and ranks system weaknesses that are up to 30 times more likely to be exploited by hackers, the Shakarians say.
The company also offers CYR3CON Screen, a web-based portal that allows analysts to find the most recent malicious hacker information from the dark web, as well as CYR3CON Alert, which provides timely and accurate intelligence to cyber defenders, and Active Threat Assessment to reveal a client’s footprint on the dark web, including related hacker discussions, industry threats and emerging attack tactics.
Tracking hackers to pre-empt cyberattacks
“What we are essentially trying to do is get ahead of the bad guys,” Paulo Shakarian explains. If you look at the major cyberattacks of recent years, he says, the vast majority were enabled by software vulnerabilities that were known about ahead of time.
The problem is that the number of vulnerabilities is growing too fast for all of them to be quickly remedied even after they are discovered.
“The people who are tasked with defending security networks don’t know where to begin,” Paulo Shakarian says. “As soon as they begin making progress there is a whole new batch of vulnerabilities that come up, so they are continually behind.”
CYR3CON provides capabilities to collect information from the hidden parts of the internet and to find out what specific vulnerabilities hackers are discovering as possible targets of attacks. Using machine learning and data mining methods, the company’s technologies can constantly search as many as 400 websites simultaneously, sifting through thousands of posts and discussions on dark web sites.
“We can say we saw these software vulnerabilities being discussed by these particular people and predict with a good degree of certainty what weaknesses of specific cybersecurity systems are going to be targeted by hackers,” Paulo Shakarian says.
Deeper look into the dark web
The Shakarians’ next step is to provide clients with strategies that quickly and precisely reinforce defenses based on a system’s specific vulnerabilities.
Along with the power of the company’s technological infrastructure, the value of its service hinges on a deep understanding of the perpetrators of malevolent cyber activity.
“To identify the bad actors in these scenarios takes knowledge of behavioral psychology,” Paulo Shakarian says. “All this hacking isn’t done by the technology itself, it’s done by people. Jana’s training as an anthropologist and sociologist comes into play in multiple aspects of what [CYR3CON] does. She knows what to focus on amid everything that’s going on out there in the hacker ecosystem.”
It’s not a matter of merely knowing what’s being talked about on the dark web.
“I don’t think you can do a good job predicting human behavior unless you have good socially rooted intuitions about what people are doing,” he says. “It’s knowing what the reputations of the people are and what their social connections look like that helps us create better algorithms to identify potential threats.”
The methodology on which the Shakarians’ enterprise is being built has been evaluated and validated by three peer-reviewed studies and has earned multiple provisional patents for ASU based on inventions by the Shakarians and various students. CYR3CON now licenses those inventions.
Business skills, more research will drive startup forward
The Shakarians have brought on experts to handle their startup’s financial, business development and customer support operations. They’re starting to bring on the company’s first customers, which range from mid-market businesses to large Fortune 500 companies.
“This will enable us to learn how our technology can be best integrated into existing operational business cybersecurity environments,” Paulo Shakarian says. “After we learn those lessons, we will expand through the use of channel partners that will resell the technology.”
CYR3CON has already established contractual relationships with multiple partners that provide complementary cybersecurity products and services.
Research aimed at improving the company’s operations and capabilities will continue. The Shakarians expect to tap into the skills of those working in Fulton Schools labs — including graduate and undergraduate students.
“Machine learning, artificial intelligence and cybersecurity are a big focus of what we teach here,” Paulo Shakarian says, “so we have an array of expertise and a large pool of talent to draw from.”
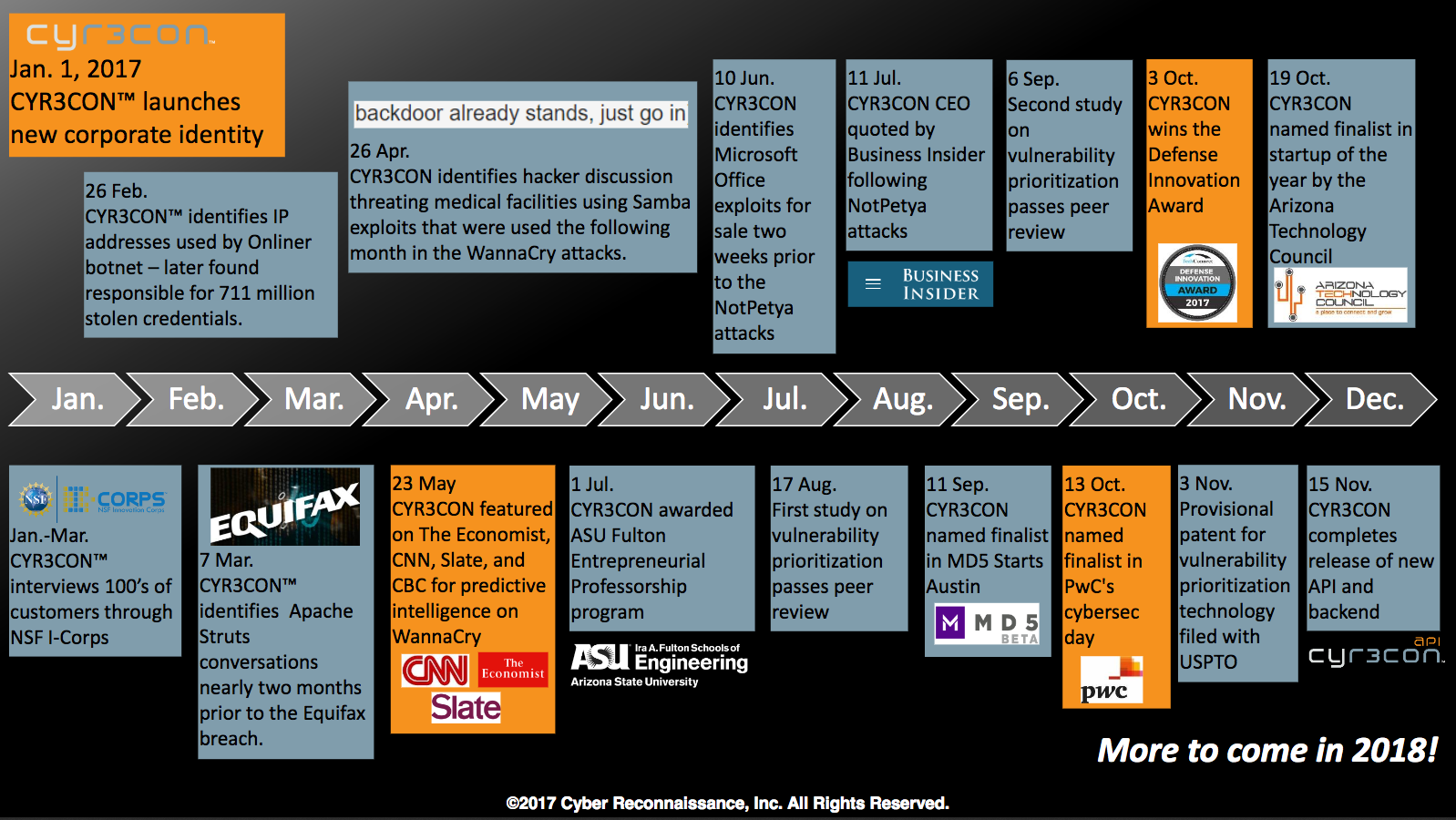
A timeline graphic traces the progress of Paulo and Jana Shakarian’s CYR3CON cybersecurity company in 2017.



































